My clients come from a diverse background, some are new to the process and others are well seasoned. 
 A default service account is created automatically for each Namespace within a cluster.
A default service account is created automatically for each Namespace within a cluster.
Brandon Talbot | Sales Representative for Cityscape Real Estate Brokerage, Brandon Talbot | Over 15 Years In Real Estate. For those that are unfamiliar, eksctl is a simple CLI tool for creating and managing clusters on EKS - Amazon's managed Kubernetes service for EC2. If such applications run on AWS infrastructure, like EC2 instances, consider using an instance profile and mapping that to a Kubernetes RBAC role in the aws-auth ConfigMap instead. For an exhaustive view into IAM users and groups, check out the full documentation from Amazon. The best way to get the ball rolling is with a no obligation, completely free consultation without a harassing bunch of follow up calls, emails and stalking. rbac.dev A list of additional resources, including blogs and tools, for Kubernetes RBAC. Built on Forem the open source software that powers DEV and other inclusive communities.
rbac.dev A list of additional resources, including blogs and tools, for Kubernetes RBAC. Built on Forem the open source software that powers DEV and other inclusive communities.  A kuberneres controller to manage the aws-auth configmap in EKS using a new AWSAuthItem CRD.
A kuberneres controller to manage the aws-auth configmap in EKS using a new AWSAuthItem CRD.  ), Directly extract any format 7zip supports to Rclone, Malicious Webhook Admission Controller in Go, Kubernetes Mutating webhook sample example, Single file version of the CAP cost calculator to run in online sandboxes, Custom driver to handle vault cred rotation, Slices tools - A module written in Golang that facilitates working with slices in Golang, Unzip the files in the folder and subfolders, then rename Chinese to Pinyin, A simple lorem ipsum generator written in Go with TDD, A telegram bot to ban channels spamming chat, Support for method call options that can be shared on multiple methods, An HTTP protocol frontend for Redis-compatible services, A developer CLI that accelerates the time it takes for you to get started on Azure. A better alternative would be to use aws-iam-authenticator to map this to a new Kubernetes group that you can attach specific RBAC bindings to: With that group, you could create RBAC Bindings with RBAC Manager that would allow you to specify access specifically for that group.
), Directly extract any format 7zip supports to Rclone, Malicious Webhook Admission Controller in Go, Kubernetes Mutating webhook sample example, Single file version of the CAP cost calculator to run in online sandboxes, Custom driver to handle vault cred rotation, Slices tools - A module written in Golang that facilitates working with slices in Golang, Unzip the files in the folder and subfolders, then rename Chinese to Pinyin, A simple lorem ipsum generator written in Go with TDD, A telegram bot to ban channels spamming chat, Support for method call options that can be shared on multiple methods, An HTTP protocol frontend for Redis-compatible services, A developer CLI that accelerates the time it takes for you to get started on Azure. A better alternative would be to use aws-iam-authenticator to map this to a new Kubernetes group that you can attach specific RBAC bindings to: With that group, you could create RBAC Bindings with RBAC Manager that would allow you to specify access specifically for that group.
"eks-developer-user-cluster-role-binding", rolearn: arn:aws:iam::017558828988:role/eks-developer, "aws:{{AccountID}}:eks-developer:{{SessionName}}", "arn:aws:iam:::user/dev-user", - userarn: arn:aws:iam:::user/dev-user. For a complete listing of the SDKs that currently support IRSA, see https://docs.aws.amazon.com/eks/latest/userguide/iam-roles-for-service-accounts-minimum-sdk.html. Since this presents a risk to your cluster, it is recommended that you update the aws-node daemonset to use IRSA. If you're using an IAM role, the actual users who assume that role aren't recorded and can't be audited. Now that we have the IAM role created, we are going to add the role to the aws-auth ConfigMap If you have single sign-on (SSO) and the ability for users to authenticate via the steps found here, then you can skip to Part II. After mapping an IAM role with mapRoles, any user or entity assuming this role is allowed to access the cluster, However, the level of access is defined by the groups attribute. Once unpublished, all posts by aws-builders will become hidden and only accessible to themselves. One of the nicest things about Terraform is that there are a plethora of public modules available. Posts for two such solutions have been published on the AWS Open Source blog: EKS natively supports OIDC authentication without using a proxy. At times, you may need to grant an exception for applications that have to consume the Kubernetes API from outside the cluster, e.g. You can also include these settings in the node group's launch template. Therefore it is a good idea to create the cluster with a dedicated IAM role and regularly audit who can assume this role. it can be accessed from the Internet. Allows super-user access to perform any action on any resource. Let's try to assume the eks-developer IAM role and try to access the cluster with that role. However, If you are using eksctl to create the cluster, this config map will have the role created by eksctl for the node group and this role is attached to the system:bootstrappers and system:nodes groups. When assigning K8s RBAC permissions to an IAM role using mapRoles in aws-auth ConfigMap, you should include {{SessionName}} in your username. An improperly formatted aws-auth ConfigMap may cause you to lose access to the cluster.  For further actions, you may consider blocking this person and/or reporting abuse. However, instead of being uniquely associated with one person, a role is intended to be assumable by anyone who needs it.". Like it or not, people other than yourself are going to have to access the cluster. By default when you provision an EKS cluster, the API cluster endpoint is set to public, i.e. Hows that going to work?". This will be easier to maintain, especially as the number of users that require access grows. With you every step of your journey.
For further actions, you may consider blocking this person and/or reporting abuse. However, instead of being uniquely associated with one person, a role is intended to be assumable by anyone who needs it.". Like it or not, people other than yourself are going to have to access the cluster. By default when you provision an EKS cluster, the API cluster endpoint is set to public, i.e. Hows that going to work?". This will be easier to maintain, especially as the number of users that require access grows. With you every step of your journey.
 Run the following command to create the developer policy: aws iam create-policy --policy-name eks-developer-assume-role-policy --policy-document file://eks-developer-assume-role-policy. The trust policy can be scoped to a Namespace or a specific service account within a Namespace. By default, this configmap is empty. This will save you from future headaches. EKS currently has native support for webhook token authentication, service account tokens, and as of February 21, 2021, OIDC authentication. Once your AWS IAM Roles are mapped to a Kubernetes user, you can create Kubernetes roles and role bindings to give permissions to various users and the AWS IAM roles they are attached to. As described in the blogs, the username/group of users authenticated by an OIDC provider will appear in the Kubernetes audit log. Although this works, it's rather inelegant and doesn't allow you to modify the access this group has with RBAC without also affecting the system:masters group. They can still re-publish the post if they are not suspended. By default, the IAM Role or IAM User that was used to create the cluster, is added to the system:masters group and gets cluster-wide admin permission with cluster-admin ClusterRole.
Run the following command to create the developer policy: aws iam create-policy --policy-name eks-developer-assume-role-policy --policy-document file://eks-developer-assume-role-policy. The trust policy can be scoped to a Namespace or a specific service account within a Namespace. By default, this configmap is empty. This will save you from future headaches. EKS currently has native support for webhook token authentication, service account tokens, and as of February 21, 2021, OIDC authentication. Once your AWS IAM Roles are mapped to a Kubernetes user, you can create Kubernetes roles and role bindings to give permissions to various users and the AWS IAM roles they are attached to. As described in the blogs, the username/group of users authenticated by an OIDC provider will appear in the Kubernetes audit log. Although this works, it's rather inelegant and doesn't allow you to modify the access this group has with RBAC without also affecting the system:masters group. They can still re-publish the post if they are not suspended. By default, the IAM Role or IAM User that was used to create the cluster, is added to the system:masters group and gets cluster-wide admin permission with cluster-admin ClusterRole.
 You can see an example terraform setup using this method inside the repository below: https://github.com/terraform-aws-modules/terraform-aws-eks/tree/v16.0.1/examples/basic. Learn more about the program and apply to join when applications are open next. Azure AD. Unflagging aws-builders will restore default visibility to their posts. When accessing the EKS cluster with the IAM entity mapped by aws-auth ConfigMap, the username described in aws-auth ConfigMap is recorded in the user field of the Kubernetes audit log. Save the following to a file and name it something along the lines of dev-role-cfg.yml, then go ahead and apply it to a namespace of your choosing. To use a non-default service account simply set the spec.serviceAccountName field of a Pod to the name of the service account you wish to use. See. We do that by creating a "RoleBinding". # Kubernetes User mapped to the IAM role in aws-auth configmap. Know that you must assume a role prior to running kubectl as the IAM role is used to determine the user's Kubernetes RBAC group.
You can see an example terraform setup using this method inside the repository below: https://github.com/terraform-aws-modules/terraform-aws-eks/tree/v16.0.1/examples/basic. Learn more about the program and apply to join when applications are open next. Azure AD. Unflagging aws-builders will restore default visibility to their posts. When accessing the EKS cluster with the IAM entity mapped by aws-auth ConfigMap, the username described in aws-auth ConfigMap is recorded in the user field of the Kubernetes audit log. Save the following to a file and name it something along the lines of dev-role-cfg.yml, then go ahead and apply it to a namespace of your choosing. To use a non-default service account simply set the spec.serviceAccountName field of a Pod to the name of the service account you wish to use. See. We do that by creating a "RoleBinding". # Kubernetes User mapped to the IAM role in aws-auth configmap. Know that you must assume a role prior to running kubectl as the IAM role is used to determine the user's Kubernetes RBAC group.  For additional information about creating service accounts, see https://kubernetes.io/docs/reference/access-authn-authz/rbac/#service-account-permissions. Finally, add the IAM users to the newly created groups with this command line input: aws iam add-user-to-group --group-name
For additional information about creating service accounts, see https://kubernetes.io/docs/reference/access-authn-authz/rbac/#service-account-permissions. Finally, add the IAM users to the newly created groups with this command line input: aws iam add-user-to-group --group-name --user-name , AWS defines an IAM role as an IAM identity that you can create in your account with specific permissions. From Amazon's documentation, IAM users represent the person or service who uses the IAM user to interact with AWS. Now we would get the AWS Account ID along with Session Name in cloudwatch logs : time="2021-09-14T18:26:33Z" level=info msg="access granted" arn="arn:aws:iam::017558828988:role/eks-developer" client="127.0.0.1:39752" groups="[developer]" method=POST path=/authenticate sts=sts.us-east-1.amazonaws.com uid="heptio-authenticator-aws:0175XXXXXXXX:AROAQIFUWO66PDOXKSLMQ" username="aws:0175XXXXXXXX:eks-developer:my-develper-session-123456789". AmazonEKS_CNI_Policy and EC2ContainerRegistryReadOnly that effectively allow all pods running on a node to attach/detach ENIs, assign/unassign IP addresses, or pull images from ECR. The value of runAsUser is arbitrary value. For additional details see https://docs.aws.amazon.com/STS/latest/APIReference/API_GetCallerIdentity.html. An alternative approach involves configuring aws-iam-authenticator to map specific IAM users to RBAC users. the user's account, Arn, and UserId to the kube-apiserver. If you have an application that is using an older version of the AWS SDK that doesn't support IRSA, and you want the pod to inherit the role assigned to the instance, consider using Kubernetes network policies to selectively allow access EC2 metadata. Here's the JSON you'll need to do that. Congratulations, you're off to a good start by asking one of the the most important questions. Run Amazon EKS on your own infrastructure, Resolv k8s nodename in cluster or k8s node, A kubectl plugin for easier query and operate k8s cluster, Example Go-based e2e benchmark for various Kubelet operations without spinning up whole K8s cluster, Kubernetes Secrets and Configmaps to dot env file.
When the application attempts to read from S3, the token is exchanged for a temporary set of IAM credentials that resembles this: A mutating webhook that runs as part of the EKS control plane injects the AWS Role ARN and the path to a web identity token file into the Pod as environment variables. aws-auth configmap is based on aws-iam-authenticator and has several configuration options: mapRoles allows mapping an IAM role in the cluster to allow any entity or user assuming that role to access the cluster. In EKS, IAM permissions are only used to check if the user has valid IAM credentials and permissions to run any command using kubectl such as kubectl get pods is managed by Kubernetes API that uses RBAC to control the access. You can learn more about it here. Go ahead and create another JSON file named eks-developer-assume-role-policy.json with the following.
A script for doing this can be found in the repository for this guide. Creating an efficient process for storing application logs is critical for cybersecurity and compliance. RBAC permissions can be assigned to this IAM role in two ways : 1. But when do you know when youve found everything you NEED? eksctl create iamidentitymapping --cluster --arn arn:aws:iam:::role/eks-admin-role --group system:masters --username eks-admin`, eksctl create iamidentitymapping --cluster --arn arn:aws:iam:::role/eks-developer-role --username eks-developer. This role should not be used to perform routine actions on the cluster, and instead additional users should be granted access to the cluster through the aws-auth ConfigMap for this purpose. IRSA is a feature that allows you to assign an IAM role to a Kubernetes service account.  As per EKS docs: EKS uses IAM permissions for authentication of valid entities such IAM users or roles. Many sales people will tell you what you want to hear and hope that you arent going to ask them to prove it. # Kubernetes User mapped to the IAM user in aws-auth configmap. It is similar to IAM Access Advisor in that it helps you gradually limit the scope of IAM roles assigned to applications. Once suspended, aws-builders will not be able to comment or publish posts until their suspension is removed. Blocking access to instance metadata will prevent pods that do not use IRSA from inheriting the role assigned to the worker node. IAM user groups are simply collections of IAM users. For further information about this method, see Limiting access to the instance metadata service.
As per EKS docs: EKS uses IAM permissions for authentication of valid entities such IAM users or roles. Many sales people will tell you what you want to hear and hope that you arent going to ask them to prove it. # Kubernetes User mapped to the IAM user in aws-auth configmap. It is similar to IAM Access Advisor in that it helps you gradually limit the scope of IAM roles assigned to applications. Once suspended, aws-builders will not be able to comment or publish posts until their suspension is removed. Blocking access to instance metadata will prevent pods that do not use IRSA from inheriting the role assigned to the worker node. IAM user groups are simply collections of IAM users. For further information about this method, see Limiting access to the instance metadata service.
 To understand what a user has access to in Kubernetes, you first have to determine what IAM roles they can assume, then what Kubernetes groups those roles map to, then what roles are bound to those Kubernetes groups. DEV Community 2016 - 2022. rolearn: arn:aws:iam::
To understand what a user has access to in Kubernetes, you first have to determine what IAM roles they can assume, then what Kubernetes groups those roles map to, then what roles are bound to those Kubernetes groups. DEV Community 2016 - 2022. rolearn: arn:aws:iam:::role/eksctl-iam-auth-cluster-nodegroup-NodeInstanceRole-1RNKIEA50ZD0B, username: system:node:{{EC2PrivateDNSName}}, "arn:aws:iam:::role/eks-developer", - rolearn: arn:aws:iam:::role/eks-developer, # Pod is part of Core API Group and "" indicates the core API group. In the following example, all processes within the Pod will run under the user ID specified in the runAsUser field. The token has a time to live (TTL) of 15 minutes after which a new token will need to be generated. Plan to periodically audit the aws-auth ConfigMap to see who has been granted access and the rights they've been assigned. In Kubernetes 1.19 and above, this change is no longer required.  The example aws-iam-authenticator configuration below uses a bit of a shortcut to use a group that already is bound to a cluster-admin role (system:masters). In all cases, the aws-iam-authenticator configuration snippets will represent part of the Kubernetes ConfigMap it reads config from. {{AccountID}} comes to the rescue, we can use this templated variable to get the AWS account ID of the user who is assuming the role, so we can set the username to : Please note that iamidentitymapping can't be overridden with eksctl, so you have to delete it and create it again.
The example aws-iam-authenticator configuration below uses a bit of a shortcut to use a group that already is bound to a cluster-admin role (system:masters). In all cases, the aws-iam-authenticator configuration snippets will represent part of the Kubernetes ConfigMap it reads config from. {{AccountID}} comes to the rescue, we can use this templated variable to get the AWS account ID of the user who is assuming the role, so we can set the username to : Please note that iamidentitymapping can't be overridden with eksctl, so you have to delete it and create it again.
EC2, or an AWS principal such as an IAM User or Role. Future plans, financial benefits and timing can be huge factors in approach. RBAC groups can be referenced in Kubernetes RoleBindings or ClusterRoleBindings. It can get quite complex to understand the level of access granted to your cluster. Next, you'll need to edit the trust relationship on each of the roles. If youd like to read more about Kubernetes RBAC, take a look at this documentation explaining user auth within the cluster.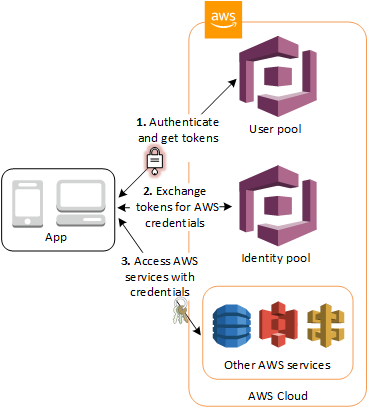 Upgrades Within AWS, a resource can be another AWS service, e.g. You can also use AWS SSO to federate AWS with an external identity provider, e.g. To check which ClusterRoles have "system:unauthenticated" except system:public-info-viewer you can run the following command (requires jq util): And "system:unauthenticated" can be removed from all the roles except "system:public-info-viewer" using: Alternatively, you can check and remove it manually by kubectl describe and kubectl edit.
Upgrades Within AWS, a resource can be another AWS service, e.g. You can also use AWS SSO to federate AWS with an external identity provider, e.g. To check which ClusterRoles have "system:unauthenticated" except system:public-info-viewer you can run the following command (requires jq util): And "system:unauthenticated" can be removed from all the roles except "system:public-info-viewer" using: Alternatively, you can check and remove it manually by kubectl describe and kubectl edit.
Note that even if you have updated your cluster to version 1.14 or higher, these permissions may still be enabled on your cluster, since cluster updates do not revoke these permissions. In order to do this, we need to create a role within the namespace, so that the user will have permissions. With EKS, this is included by default, and it's fairly straightforward to setup with Kops (opens new window) or other methods of cluster provisioning. With the above config you could specify RBAC Bindings with the following RBAC Definition: Although we no longer need to understand which AWS IAM users can assume specific IAM roles. Review the aws-auth docs on GitHub for more information, including the go library. There are a few options here, depending on how you deployed your cluster: Terraform is a software based infrastructure as code tool developed by Hashicorp that we highly recommend for all projects to help retain clear and concise definitions for cloud infrastructure. On AWS, we recommend using aws-iam-authenticator (opens new window) for Kubernetes authentication. ConfigMap. Again, make sure you change the ACCOUNT_ID variable to your AWS account id. This signed token allows the Pod to call the AWS APIs associated IAM role. It works by leveraging a Kubernetes feature known as Service Account Token Volume Projection. From Part I, you should now be able to assume a role in AWS IAM via either SSO or AWS IAM Groups. They are similar to IAM Roles in that they define a set of actions (verbs) that can be performed against a collection of Kubernetes resources (objects). For an example showing how to configure EKS with Dex, a popular open source OIDC provider with connectors for a variety of different authention methods, see Using Dex & dex-k8s-authenticator to authenticate to Amazon EKS. followed by a base64 encoded string. Now we need to create the developer assume role policy. "sigs.k8s.io/aws-iam-authenticator/pkg/token", "k8s-aws-v1.aHR0cHM6Ly9zdHMuYW1hem9uYXdzLmNvbS8_QWN0aW9uPUdldENhbGxlcklkZW50aXR5JlZlcnNpb249MjAxMS0wNi0xNSZYLUFtei1BbGdvcml0aG09QVdTNC1ITUFDLVNIQTI1NiZYLUFtei1DcmVkZW50aWFsPUFLSUFKTkdSSUxLTlNSQzJXNVFBJTJGMjAyMDAyMTklMkZ1cy1lYXN0LTElMkZzdHMlMkZhd3M0X3JlcXVlc3QmWC1BbXotRGF0ZT0yMDIwMDIxOVQxNTU0MjdaJlgtQW16LUV4cGlyZXM9NjAmWC1BbXotU2lnbmVkSGVhZGVycz1ob3N0JTNCeC1rOHMtYXdzLWlkJlgtQW16LVNpZ25hdHVyZT0yMjBmOGYzNTg1ZTMyMGRkYjVlNjgzYTVjOWE0MDUzMDFhZDc2NTQ2ZjI0ZjI4MTExZmRhZDA5Y2Y2NDhhMzkz", "kubernetes.io/serviceaccount/secret.name", "kubernetes.io/serviceaccount/service-account.name", "kubernetes.io/serviceaccount/service-account.uid", rbac.authorization.kubernetes.io/autoupdate, /apis/rbac.authorization.k8s.io/v1/clusterroles/system%3Adiscovery, "https://oidc.eks.us-west-2.amazonaws.com/id/D43CF17C27A865933144EA99A26FB128", "system:serviceaccount:default:s3-read-only", "arn:aws:sts::123456789012:assumed-role/eksctl-winterfell-addon-iamserviceaccount-de-Role1-1D61LT75JH3MB/abc", "arn:aws:iam::123456789012:oidc-provider/oidc.eks.us-west-2.amazonaws.com/id/D43CF17C27A865933144EA99A26FB128", "ORJ+8Adk+wW+nU8FETq7+mOqeA8Z6jlPihnV8hX1", "FwoGZXIvYXdzEGMaDMLxAZkuLpmSwYXShiL9A1S0X87VBC1mHCrRe/pB2oes+l1eXxUYnPJyC9ayOoXMvqXQsomq0xs6OqZ3vaa5Iw1HIyA4Cv1suLaOCoU3hNvOIJ6C94H1vU0siQYk7DIq9Av5RZe+uE2FnOctNBvYLd3i0IZo1ajjc00yRK3v24VRq9nQpoPLuqyH2jzlhCEjXuPScPbi5KEVs9fNcOTtgzbVf7IG2gNiwNs5aCpN4Bv/Zv2A6zp5xGz9cWj2f0aD9v66vX4bexOs5t/YYhwuwAvkkJPSIGvxja0xRThnceHyFHKtj0H+bi/PWAtlI8YJcDX69cM30JAHDdQH+ltm/4scFptW1hlvMaP+WReCAaCrsHrAT+yka7ttw5YlUyvZ8EPog+j6fwHlxmrXM9h1BqdikomyJU00gm1++FJelfP+1zAwcyrxCnbRl3ARFrAt8hIlrT6Vyu8WvWtLxcI8KcLcJQb/LgkW+sCTGlYcY8z3zkigJMbYn07ewTL5Ss7LazTJJa758I7PZan/v3xQHd5DEc5WBneiV3iOznDFgup0VAMkIviVjVCkszaPSVEdK2NU7jtrh6Jfm7bU/3P6ZG+CkyDLIa8MBn9KPXeJd/y+jTk5Ii+fIwO/+mDpGNUribg6TPxhzZ8b/XdZO1kS1gVgqjXyVC+M+BRBh6C4H21w/eMzjCtDIpoxt5rGKL6Nu/IFMipoC4fgx6LIIHwtGYMG7SWQi7OsMAkiwZRg0n68/RqWgLzBt/4pfjSRYuk=", Don't use a service account token for authentication, Employ least privileged access to AWS Resources, Use IAM Roles when multiple users need identical access to the cluster, Employ least privileged access when creating RoleBindings and ClusterRoleBindings, Create the cluster with a dedicated IAM role, Use tools to make changes to the aws-auth ConfigMap, Alternative Approaches to Authentication and Access Management, Update the aws-node daemonset to use IRSA, Restrict access to the instance profile assigned to the worker node, Scope the IAM Role trust policy for IRSA to the service account name, When your application needs access to IMDS, use IMDSv2 and increase the hop limit on EC2 instances to 2, Disable auto-mounting of service account tokens, Use dedicated service accounts for each application, Grant least privileged access to applications, Review and revoke unnecessary anonymous access, https://docs.aws.amazon.com/STS/latest/APIReference/API_GetCallerIdentity.html, Authenticating to EKS Using GitHub Credentials with Teleport, Consistent OIDC authentication across multiple EKS clusters using kube-oidc-proxy, Introducing OIDC identity provider authentication for Amazon EKS, Using Dex & dex-k8s-authenticator to authenticate to Amazon EKS, https://kubernetes.io/docs/reference/access-authn-authz/rbac/#service-account-permissions, https://docs.aws.amazon.com/eks/latest/userguide/iam-roles-for-service-accounts-technical-overview.html, Limiting access to the instance metadata service, https://eksctl.io/usage/iamserviceaccounts/, https://docs.aws.amazon.com/eks/latest/userguide/iam-roles-for-service-accounts-minimum-sdk.html, Configure the EKS cluster endpoint to be private. If the request is well-formed, the webhook calls a pre-signed URL embedded in the token's body. Now lets get into the specifics of setting this part up. First, start by creating two IAM roles named eks-admin-role and eks-developer-role with the following CLI commands: aws iam create-role --role-name eks-admin-role --output text --query 'Role.Arn', aws iam create-role --role-name eks-developer-role --output text --query 'Role.Arn'. # Allow user to get, list of watch the pods. Once unsuspended, aws-builders will be able to comment and publish posts again. The controller also needs to be able to invoke AWS APIs to provision and configure an ALB.
"sigs.k8s.io/aws-iam-authenticator/pkg/token", "k8s-aws-v1.aHR0cHM6Ly9zdHMuYW1hem9uYXdzLmNvbS8_QWN0aW9uPUdldENhbGxlcklkZW50aXR5JlZlcnNpb249MjAxMS0wNi0xNSZYLUFtei1BbGdvcml0aG09QVdTNC1ITUFDLVNIQTI1NiZYLUFtei1DcmVkZW50aWFsPUFLSUFKTkdSSUxLTlNSQzJXNVFBJTJGMjAyMDAyMTklMkZ1cy1lYXN0LTElMkZzdHMlMkZhd3M0X3JlcXVlc3QmWC1BbXotRGF0ZT0yMDIwMDIxOVQxNTU0MjdaJlgtQW16LUV4cGlyZXM9NjAmWC1BbXotU2lnbmVkSGVhZGVycz1ob3N0JTNCeC1rOHMtYXdzLWlkJlgtQW16LVNpZ25hdHVyZT0yMjBmOGYzNTg1ZTMyMGRkYjVlNjgzYTVjOWE0MDUzMDFhZDc2NTQ2ZjI0ZjI4MTExZmRhZDA5Y2Y2NDhhMzkz", "kubernetes.io/serviceaccount/secret.name", "kubernetes.io/serviceaccount/service-account.name", "kubernetes.io/serviceaccount/service-account.uid", rbac.authorization.kubernetes.io/autoupdate, /apis/rbac.authorization.k8s.io/v1/clusterroles/system%3Adiscovery, "https://oidc.eks.us-west-2.amazonaws.com/id/D43CF17C27A865933144EA99A26FB128", "system:serviceaccount:default:s3-read-only", "arn:aws:sts::123456789012:assumed-role/eksctl-winterfell-addon-iamserviceaccount-de-Role1-1D61LT75JH3MB/abc", "arn:aws:iam::123456789012:oidc-provider/oidc.eks.us-west-2.amazonaws.com/id/D43CF17C27A865933144EA99A26FB128", "ORJ+8Adk+wW+nU8FETq7+mOqeA8Z6jlPihnV8hX1", "FwoGZXIvYXdzEGMaDMLxAZkuLpmSwYXShiL9A1S0X87VBC1mHCrRe/pB2oes+l1eXxUYnPJyC9ayOoXMvqXQsomq0xs6OqZ3vaa5Iw1HIyA4Cv1suLaOCoU3hNvOIJ6C94H1vU0siQYk7DIq9Av5RZe+uE2FnOctNBvYLd3i0IZo1ajjc00yRK3v24VRq9nQpoPLuqyH2jzlhCEjXuPScPbi5KEVs9fNcOTtgzbVf7IG2gNiwNs5aCpN4Bv/Zv2A6zp5xGz9cWj2f0aD9v66vX4bexOs5t/YYhwuwAvkkJPSIGvxja0xRThnceHyFHKtj0H+bi/PWAtlI8YJcDX69cM30JAHDdQH+ltm/4scFptW1hlvMaP+WReCAaCrsHrAT+yka7ttw5YlUyvZ8EPog+j6fwHlxmrXM9h1BqdikomyJU00gm1++FJelfP+1zAwcyrxCnbRl3ARFrAt8hIlrT6Vyu8WvWtLxcI8KcLcJQb/LgkW+sCTGlYcY8z3zkigJMbYn07ewTL5Ss7LazTJJa758I7PZan/v3xQHd5DEc5WBneiV3iOznDFgup0VAMkIviVjVCkszaPSVEdK2NU7jtrh6Jfm7bU/3P6ZG+CkyDLIa8MBn9KPXeJd/y+jTk5Ii+fIwO/+mDpGNUribg6TPxhzZ8b/XdZO1kS1gVgqjXyVC+M+BRBh6C4H21w/eMzjCtDIpoxt5rGKL6Nu/IFMipoC4fgx6LIIHwtGYMG7SWQi7OsMAkiwZRg0n68/RqWgLzBt/4pfjSRYuk=", Don't use a service account token for authentication, Employ least privileged access to AWS Resources, Use IAM Roles when multiple users need identical access to the cluster, Employ least privileged access when creating RoleBindings and ClusterRoleBindings, Create the cluster with a dedicated IAM role, Use tools to make changes to the aws-auth ConfigMap, Alternative Approaches to Authentication and Access Management, Update the aws-node daemonset to use IRSA, Restrict access to the instance profile assigned to the worker node, Scope the IAM Role trust policy for IRSA to the service account name, When your application needs access to IMDS, use IMDSv2 and increase the hop limit on EC2 instances to 2, Disable auto-mounting of service account tokens, Use dedicated service accounts for each application, Grant least privileged access to applications, Review and revoke unnecessary anonymous access, https://docs.aws.amazon.com/STS/latest/APIReference/API_GetCallerIdentity.html, Authenticating to EKS Using GitHub Credentials with Teleport, Consistent OIDC authentication across multiple EKS clusters using kube-oidc-proxy, Introducing OIDC identity provider authentication for Amazon EKS, Using Dex & dex-k8s-authenticator to authenticate to Amazon EKS, https://kubernetes.io/docs/reference/access-authn-authz/rbac/#service-account-permissions, https://docs.aws.amazon.com/eks/latest/userguide/iam-roles-for-service-accounts-technical-overview.html, Limiting access to the instance metadata service, https://eksctl.io/usage/iamserviceaccounts/, https://docs.aws.amazon.com/eks/latest/userguide/iam-roles-for-service-accounts-minimum-sdk.html, Configure the EKS cluster endpoint to be private. If the request is well-formed, the webhook calls a pre-signed URL embedded in the token's body. Now lets get into the specifics of setting this part up. First, start by creating two IAM roles named eks-admin-role and eks-developer-role with the following CLI commands: aws iam create-role --role-name eks-admin-role --output text --query 'Role.Arn', aws iam create-role --role-name eks-developer-role --output text --query 'Role.Arn'. # Allow user to get, list of watch the pods. Once unsuspended, aws-builders will be able to comment and publish posts again. The controller also needs to be able to invoke AWS APIs to provision and configure an ALB.  If you decide to use this, the AWS CLI v2.0 includes an option to create a named profile that makes it easy to associate an SSO session with your current CLI session and assume an IAM role.
If you decide to use this, the AWS CLI v2.0 includes an option to create a named profile that makes it easy to associate an SSO session with your current CLI session and assume an IAM role.
While this allows them to read the web identity token file, running a container as root is not considered a best practice.

 A default service account is created automatically for each Namespace within a cluster.
A default service account is created automatically for each Namespace within a cluster. Brandon Talbot | Sales Representative for Cityscape Real Estate Brokerage, Brandon Talbot | Over 15 Years In Real Estate. For those that are unfamiliar, eksctl is a simple CLI tool for creating and managing clusters on EKS - Amazon's managed Kubernetes service for EC2. If such applications run on AWS infrastructure, like EC2 instances, consider using an instance profile and mapping that to a Kubernetes RBAC role in the aws-auth ConfigMap instead. For an exhaustive view into IAM users and groups, check out the full documentation from Amazon. The best way to get the ball rolling is with a no obligation, completely free consultation without a harassing bunch of follow up calls, emails and stalking.
 rbac.dev A list of additional resources, including blogs and tools, for Kubernetes RBAC. Built on Forem the open source software that powers DEV and other inclusive communities.
rbac.dev A list of additional resources, including blogs and tools, for Kubernetes RBAC. Built on Forem the open source software that powers DEV and other inclusive communities.  A kuberneres controller to manage the aws-auth configmap in EKS using a new AWSAuthItem CRD.
A kuberneres controller to manage the aws-auth configmap in EKS using a new AWSAuthItem CRD.  ), Directly extract any format 7zip supports to Rclone, Malicious Webhook Admission Controller in Go, Kubernetes Mutating webhook sample example, Single file version of the CAP cost calculator to run in online sandboxes, Custom driver to handle vault cred rotation, Slices tools - A module written in Golang that facilitates working with slices in Golang, Unzip the files in the folder and subfolders, then rename Chinese to Pinyin, A simple lorem ipsum generator written in Go with TDD, A telegram bot to ban channels spamming chat, Support for method call options that can be shared on multiple methods, An HTTP protocol frontend for Redis-compatible services, A developer CLI that accelerates the time it takes for you to get started on Azure. A better alternative would be to use aws-iam-authenticator to map this to a new Kubernetes group that you can attach specific RBAC bindings to: With that group, you could create RBAC Bindings with RBAC Manager that would allow you to specify access specifically for that group.
), Directly extract any format 7zip supports to Rclone, Malicious Webhook Admission Controller in Go, Kubernetes Mutating webhook sample example, Single file version of the CAP cost calculator to run in online sandboxes, Custom driver to handle vault cred rotation, Slices tools - A module written in Golang that facilitates working with slices in Golang, Unzip the files in the folder and subfolders, then rename Chinese to Pinyin, A simple lorem ipsum generator written in Go with TDD, A telegram bot to ban channels spamming chat, Support for method call options that can be shared on multiple methods, An HTTP protocol frontend for Redis-compatible services, A developer CLI that accelerates the time it takes for you to get started on Azure. A better alternative would be to use aws-iam-authenticator to map this to a new Kubernetes group that you can attach specific RBAC bindings to: With that group, you could create RBAC Bindings with RBAC Manager that would allow you to specify access specifically for that group. "eks-developer-user-cluster-role-binding", rolearn: arn:aws:iam::017558828988:role/eks-developer, "aws:{{AccountID}}:eks-developer:{{SessionName}}", "arn:aws:iam::
 For further actions, you may consider blocking this person and/or reporting abuse. However, instead of being uniquely associated with one person, a role is intended to be assumable by anyone who needs it.". Like it or not, people other than yourself are going to have to access the cluster. By default when you provision an EKS cluster, the API cluster endpoint is set to public, i.e. Hows that going to work?". This will be easier to maintain, especially as the number of users that require access grows. With you every step of your journey.
For further actions, you may consider blocking this person and/or reporting abuse. However, instead of being uniquely associated with one person, a role is intended to be assumable by anyone who needs it.". Like it or not, people other than yourself are going to have to access the cluster. By default when you provision an EKS cluster, the API cluster endpoint is set to public, i.e. Hows that going to work?". This will be easier to maintain, especially as the number of users that require access grows. With you every step of your journey.  Run the following command to create the developer policy: aws iam create-policy --policy-name eks-developer-assume-role-policy --policy-document file://eks-developer-assume-role-policy. The trust policy can be scoped to a Namespace or a specific service account within a Namespace. By default, this configmap is empty. This will save you from future headaches. EKS currently has native support for webhook token authentication, service account tokens, and as of February 21, 2021, OIDC authentication. Once your AWS IAM Roles are mapped to a Kubernetes user, you can create Kubernetes roles and role bindings to give permissions to various users and the AWS IAM roles they are attached to. As described in the blogs, the username/group of users authenticated by an OIDC provider will appear in the Kubernetes audit log. Although this works, it's rather inelegant and doesn't allow you to modify the access this group has with RBAC without also affecting the system:masters group. They can still re-publish the post if they are not suspended. By default, the IAM Role or IAM User that was used to create the cluster, is added to the system:masters group and gets cluster-wide admin permission with cluster-admin ClusterRole.
Run the following command to create the developer policy: aws iam create-policy --policy-name eks-developer-assume-role-policy --policy-document file://eks-developer-assume-role-policy. The trust policy can be scoped to a Namespace or a specific service account within a Namespace. By default, this configmap is empty. This will save you from future headaches. EKS currently has native support for webhook token authentication, service account tokens, and as of February 21, 2021, OIDC authentication. Once your AWS IAM Roles are mapped to a Kubernetes user, you can create Kubernetes roles and role bindings to give permissions to various users and the AWS IAM roles they are attached to. As described in the blogs, the username/group of users authenticated by an OIDC provider will appear in the Kubernetes audit log. Although this works, it's rather inelegant and doesn't allow you to modify the access this group has with RBAC without also affecting the system:masters group. They can still re-publish the post if they are not suspended. By default, the IAM Role or IAM User that was used to create the cluster, is added to the system:masters group and gets cluster-wide admin permission with cluster-admin ClusterRole.  You can see an example terraform setup using this method inside the repository below: https://github.com/terraform-aws-modules/terraform-aws-eks/tree/v16.0.1/examples/basic. Learn more about the program and apply to join when applications are open next. Azure AD. Unflagging aws-builders will restore default visibility to their posts. When accessing the EKS cluster with the IAM entity mapped by aws-auth ConfigMap, the username described in aws-auth ConfigMap is recorded in the user field of the Kubernetes audit log. Save the following to a file and name it something along the lines of dev-role-cfg.yml, then go ahead and apply it to a namespace of your choosing. To use a non-default service account simply set the spec.serviceAccountName field of a Pod to the name of the service account you wish to use. See. We do that by creating a "RoleBinding". # Kubernetes User mapped to the IAM role in aws-auth configmap. Know that you must assume a role prior to running kubectl as the IAM role is used to determine the user's Kubernetes RBAC group.
You can see an example terraform setup using this method inside the repository below: https://github.com/terraform-aws-modules/terraform-aws-eks/tree/v16.0.1/examples/basic. Learn more about the program and apply to join when applications are open next. Azure AD. Unflagging aws-builders will restore default visibility to their posts. When accessing the EKS cluster with the IAM entity mapped by aws-auth ConfigMap, the username described in aws-auth ConfigMap is recorded in the user field of the Kubernetes audit log. Save the following to a file and name it something along the lines of dev-role-cfg.yml, then go ahead and apply it to a namespace of your choosing. To use a non-default service account simply set the spec.serviceAccountName field of a Pod to the name of the service account you wish to use. See. We do that by creating a "RoleBinding". # Kubernetes User mapped to the IAM role in aws-auth configmap. Know that you must assume a role prior to running kubectl as the IAM role is used to determine the user's Kubernetes RBAC group.  For additional information about creating service accounts, see https://kubernetes.io/docs/reference/access-authn-authz/rbac/#service-account-permissions. Finally, add the IAM users to the newly created groups with this command line input: aws iam add-user-to-group --group-name
For additional information about creating service accounts, see https://kubernetes.io/docs/reference/access-authn-authz/rbac/#service-account-permissions. Finally, add the IAM users to the newly created groups with this command line input: aws iam add-user-to-group --group-name When the application attempts to read from S3, the token is exchanged for a temporary set of IAM credentials that resembles this: A mutating webhook that runs as part of the EKS control plane injects the AWS Role ARN and the path to a web identity token file into the Pod as environment variables. aws-auth configmap is based on aws-iam-authenticator and has several configuration options: mapRoles allows mapping an IAM role in the cluster to allow any entity or user assuming that role to access the cluster. In EKS, IAM permissions are only used to check if the user has valid IAM credentials and permissions to run any command using kubectl such as kubectl get pods is managed by Kubernetes API that uses RBAC to control the access. You can learn more about it here. Go ahead and create another JSON file named eks-developer-assume-role-policy.json with the following.
A script for doing this can be found in the repository for this guide. Creating an efficient process for storing application logs is critical for cybersecurity and compliance. RBAC permissions can be assigned to this IAM role in two ways : 1. But when do you know when youve found everything you NEED? eksctl create iamidentitymapping --cluster
 As per EKS docs: EKS uses IAM permissions for authentication of valid entities such IAM users or roles. Many sales people will tell you what you want to hear and hope that you arent going to ask them to prove it. # Kubernetes User mapped to the IAM user in aws-auth configmap. It is similar to IAM Access Advisor in that it helps you gradually limit the scope of IAM roles assigned to applications. Once suspended, aws-builders will not be able to comment or publish posts until their suspension is removed. Blocking access to instance metadata will prevent pods that do not use IRSA from inheriting the role assigned to the worker node. IAM user groups are simply collections of IAM users. For further information about this method, see Limiting access to the instance metadata service.
As per EKS docs: EKS uses IAM permissions for authentication of valid entities such IAM users or roles. Many sales people will tell you what you want to hear and hope that you arent going to ask them to prove it. # Kubernetes User mapped to the IAM user in aws-auth configmap. It is similar to IAM Access Advisor in that it helps you gradually limit the scope of IAM roles assigned to applications. Once suspended, aws-builders will not be able to comment or publish posts until their suspension is removed. Blocking access to instance metadata will prevent pods that do not use IRSA from inheriting the role assigned to the worker node. IAM user groups are simply collections of IAM users. For further information about this method, see Limiting access to the instance metadata service.  To understand what a user has access to in Kubernetes, you first have to determine what IAM roles they can assume, then what Kubernetes groups those roles map to, then what roles are bound to those Kubernetes groups. DEV Community 2016 - 2022. rolearn: arn:aws:iam::
To understand what a user has access to in Kubernetes, you first have to determine what IAM roles they can assume, then what Kubernetes groups those roles map to, then what roles are bound to those Kubernetes groups. DEV Community 2016 - 2022. rolearn: arn:aws:iam:: The example aws-iam-authenticator configuration below uses a bit of a shortcut to use a group that already is bound to a cluster-admin role (system:masters). In all cases, the aws-iam-authenticator configuration snippets will represent part of the Kubernetes ConfigMap it reads config from. {{AccountID}} comes to the rescue, we can use this templated variable to get the AWS account ID of the user who is assuming the role, so we can set the username to : Please note that iamidentitymapping can't be overridden with eksctl, so you have to delete it and create it again.
The example aws-iam-authenticator configuration below uses a bit of a shortcut to use a group that already is bound to a cluster-admin role (system:masters). In all cases, the aws-iam-authenticator configuration snippets will represent part of the Kubernetes ConfigMap it reads config from. {{AccountID}} comes to the rescue, we can use this templated variable to get the AWS account ID of the user who is assuming the role, so we can set the username to : Please note that iamidentitymapping can't be overridden with eksctl, so you have to delete it and create it again. EC2, or an AWS principal such as an IAM User or Role. Future plans, financial benefits and timing can be huge factors in approach. RBAC groups can be referenced in Kubernetes RoleBindings or ClusterRoleBindings. It can get quite complex to understand the level of access granted to your cluster. Next, you'll need to edit the trust relationship on each of the roles. If youd like to read more about Kubernetes RBAC, take a look at this documentation explaining user auth within the cluster.
 Upgrades Within AWS, a resource can be another AWS service, e.g. You can also use AWS SSO to federate AWS with an external identity provider, e.g. To check which ClusterRoles have "system:unauthenticated" except system:public-info-viewer you can run the following command (requires jq util): And "system:unauthenticated" can be removed from all the roles except "system:public-info-viewer" using: Alternatively, you can check and remove it manually by kubectl describe and kubectl edit.
Upgrades Within AWS, a resource can be another AWS service, e.g. You can also use AWS SSO to federate AWS with an external identity provider, e.g. To check which ClusterRoles have "system:unauthenticated" except system:public-info-viewer you can run the following command (requires jq util): And "system:unauthenticated" can be removed from all the roles except "system:public-info-viewer" using: Alternatively, you can check and remove it manually by kubectl describe and kubectl edit. Note that even if you have updated your cluster to version 1.14 or higher, these permissions may still be enabled on your cluster, since cluster updates do not revoke these permissions. In order to do this, we need to create a role within the namespace, so that the user will have permissions. With EKS, this is included by default, and it's fairly straightforward to setup with Kops (opens new window) or other methods of cluster provisioning. With the above config you could specify RBAC Bindings with the following RBAC Definition: Although we no longer need to understand which AWS IAM users can assume specific IAM roles. Review the aws-auth docs on GitHub for more information, including the go library. There are a few options here, depending on how you deployed your cluster: Terraform is a software based infrastructure as code tool developed by Hashicorp that we highly recommend for all projects to help retain clear and concise definitions for cloud infrastructure. On AWS, we recommend using aws-iam-authenticator (opens new window) for Kubernetes authentication. ConfigMap. Again, make sure you change the ACCOUNT_ID variable to your AWS account id. This signed token allows the Pod to call the AWS APIs associated IAM role. It works by leveraging a Kubernetes feature known as Service Account Token Volume Projection. From Part I, you should now be able to assume a role in AWS IAM via either SSO or AWS IAM Groups. They are similar to IAM Roles in that they define a set of actions (verbs) that can be performed against a collection of Kubernetes resources (objects). For an example showing how to configure EKS with Dex, a popular open source OIDC provider with connectors for a variety of different authention methods, see Using Dex & dex-k8s-authenticator to authenticate to Amazon EKS. followed by a base64 encoded string. Now we need to create the developer assume role policy.
 "sigs.k8s.io/aws-iam-authenticator/pkg/token", "k8s-aws-v1.aHR0cHM6Ly9zdHMuYW1hem9uYXdzLmNvbS8_QWN0aW9uPUdldENhbGxlcklkZW50aXR5JlZlcnNpb249MjAxMS0wNi0xNSZYLUFtei1BbGdvcml0aG09QVdTNC1ITUFDLVNIQTI1NiZYLUFtei1DcmVkZW50aWFsPUFLSUFKTkdSSUxLTlNSQzJXNVFBJTJGMjAyMDAyMTklMkZ1cy1lYXN0LTElMkZzdHMlMkZhd3M0X3JlcXVlc3QmWC1BbXotRGF0ZT0yMDIwMDIxOVQxNTU0MjdaJlgtQW16LUV4cGlyZXM9NjAmWC1BbXotU2lnbmVkSGVhZGVycz1ob3N0JTNCeC1rOHMtYXdzLWlkJlgtQW16LVNpZ25hdHVyZT0yMjBmOGYzNTg1ZTMyMGRkYjVlNjgzYTVjOWE0MDUzMDFhZDc2NTQ2ZjI0ZjI4MTExZmRhZDA5Y2Y2NDhhMzkz", "kubernetes.io/serviceaccount/secret.name", "kubernetes.io/serviceaccount/service-account.name", "kubernetes.io/serviceaccount/service-account.uid", rbac.authorization.kubernetes.io/autoupdate, /apis/rbac.authorization.k8s.io/v1/clusterroles/system%3Adiscovery, "https://oidc.eks.us-west-2.amazonaws.com/id/D43CF17C27A865933144EA99A26FB128", "system:serviceaccount:default:s3-read-only", "arn:aws:sts::123456789012:assumed-role/eksctl-winterfell-addon-iamserviceaccount-de-Role1-1D61LT75JH3MB/abc", "arn:aws:iam::123456789012:oidc-provider/oidc.eks.us-west-2.amazonaws.com/id/D43CF17C27A865933144EA99A26FB128", "ORJ+8Adk+wW+nU8FETq7+mOqeA8Z6jlPihnV8hX1", "FwoGZXIvYXdzEGMaDMLxAZkuLpmSwYXShiL9A1S0X87VBC1mHCrRe/pB2oes+l1eXxUYnPJyC9ayOoXMvqXQsomq0xs6OqZ3vaa5Iw1HIyA4Cv1suLaOCoU3hNvOIJ6C94H1vU0siQYk7DIq9Av5RZe+uE2FnOctNBvYLd3i0IZo1ajjc00yRK3v24VRq9nQpoPLuqyH2jzlhCEjXuPScPbi5KEVs9fNcOTtgzbVf7IG2gNiwNs5aCpN4Bv/Zv2A6zp5xGz9cWj2f0aD9v66vX4bexOs5t/YYhwuwAvkkJPSIGvxja0xRThnceHyFHKtj0H+bi/PWAtlI8YJcDX69cM30JAHDdQH+ltm/4scFptW1hlvMaP+WReCAaCrsHrAT+yka7ttw5YlUyvZ8EPog+j6fwHlxmrXM9h1BqdikomyJU00gm1++FJelfP+1zAwcyrxCnbRl3ARFrAt8hIlrT6Vyu8WvWtLxcI8KcLcJQb/LgkW+sCTGlYcY8z3zkigJMbYn07ewTL5Ss7LazTJJa758I7PZan/v3xQHd5DEc5WBneiV3iOznDFgup0VAMkIviVjVCkszaPSVEdK2NU7jtrh6Jfm7bU/3P6ZG+CkyDLIa8MBn9KPXeJd/y+jTk5Ii+fIwO/+mDpGNUribg6TPxhzZ8b/XdZO1kS1gVgqjXyVC+M+BRBh6C4H21w/eMzjCtDIpoxt5rGKL6Nu/IFMipoC4fgx6LIIHwtGYMG7SWQi7OsMAkiwZRg0n68/RqWgLzBt/4pfjSRYuk=", Don't use a service account token for authentication, Employ least privileged access to AWS Resources, Use IAM Roles when multiple users need identical access to the cluster, Employ least privileged access when creating RoleBindings and ClusterRoleBindings, Create the cluster with a dedicated IAM role, Use tools to make changes to the aws-auth ConfigMap, Alternative Approaches to Authentication and Access Management, Update the aws-node daemonset to use IRSA, Restrict access to the instance profile assigned to the worker node, Scope the IAM Role trust policy for IRSA to the service account name, When your application needs access to IMDS, use IMDSv2 and increase the hop limit on EC2 instances to 2, Disable auto-mounting of service account tokens, Use dedicated service accounts for each application, Grant least privileged access to applications, Review and revoke unnecessary anonymous access, https://docs.aws.amazon.com/STS/latest/APIReference/API_GetCallerIdentity.html, Authenticating to EKS Using GitHub Credentials with Teleport, Consistent OIDC authentication across multiple EKS clusters using kube-oidc-proxy, Introducing OIDC identity provider authentication for Amazon EKS, Using Dex & dex-k8s-authenticator to authenticate to Amazon EKS, https://kubernetes.io/docs/reference/access-authn-authz/rbac/#service-account-permissions, https://docs.aws.amazon.com/eks/latest/userguide/iam-roles-for-service-accounts-technical-overview.html, Limiting access to the instance metadata service, https://eksctl.io/usage/iamserviceaccounts/, https://docs.aws.amazon.com/eks/latest/userguide/iam-roles-for-service-accounts-minimum-sdk.html, Configure the EKS cluster endpoint to be private. If the request is well-formed, the webhook calls a pre-signed URL embedded in the token's body. Now lets get into the specifics of setting this part up. First, start by creating two IAM roles named eks-admin-role and eks-developer-role with the following CLI commands: aws iam create-role --role-name eks-admin-role --output text --query 'Role.Arn', aws iam create-role --role-name eks-developer-role --output text --query 'Role.Arn'. # Allow user to get, list of watch the pods. Once unsuspended, aws-builders will be able to comment and publish posts again. The controller also needs to be able to invoke AWS APIs to provision and configure an ALB.
"sigs.k8s.io/aws-iam-authenticator/pkg/token", "k8s-aws-v1.aHR0cHM6Ly9zdHMuYW1hem9uYXdzLmNvbS8_QWN0aW9uPUdldENhbGxlcklkZW50aXR5JlZlcnNpb249MjAxMS0wNi0xNSZYLUFtei1BbGdvcml0aG09QVdTNC1ITUFDLVNIQTI1NiZYLUFtei1DcmVkZW50aWFsPUFLSUFKTkdSSUxLTlNSQzJXNVFBJTJGMjAyMDAyMTklMkZ1cy1lYXN0LTElMkZzdHMlMkZhd3M0X3JlcXVlc3QmWC1BbXotRGF0ZT0yMDIwMDIxOVQxNTU0MjdaJlgtQW16LUV4cGlyZXM9NjAmWC1BbXotU2lnbmVkSGVhZGVycz1ob3N0JTNCeC1rOHMtYXdzLWlkJlgtQW16LVNpZ25hdHVyZT0yMjBmOGYzNTg1ZTMyMGRkYjVlNjgzYTVjOWE0MDUzMDFhZDc2NTQ2ZjI0ZjI4MTExZmRhZDA5Y2Y2NDhhMzkz", "kubernetes.io/serviceaccount/secret.name", "kubernetes.io/serviceaccount/service-account.name", "kubernetes.io/serviceaccount/service-account.uid", rbac.authorization.kubernetes.io/autoupdate, /apis/rbac.authorization.k8s.io/v1/clusterroles/system%3Adiscovery, "https://oidc.eks.us-west-2.amazonaws.com/id/D43CF17C27A865933144EA99A26FB128", "system:serviceaccount:default:s3-read-only", "arn:aws:sts::123456789012:assumed-role/eksctl-winterfell-addon-iamserviceaccount-de-Role1-1D61LT75JH3MB/abc", "arn:aws:iam::123456789012:oidc-provider/oidc.eks.us-west-2.amazonaws.com/id/D43CF17C27A865933144EA99A26FB128", "ORJ+8Adk+wW+nU8FETq7+mOqeA8Z6jlPihnV8hX1", "FwoGZXIvYXdzEGMaDMLxAZkuLpmSwYXShiL9A1S0X87VBC1mHCrRe/pB2oes+l1eXxUYnPJyC9ayOoXMvqXQsomq0xs6OqZ3vaa5Iw1HIyA4Cv1suLaOCoU3hNvOIJ6C94H1vU0siQYk7DIq9Av5RZe+uE2FnOctNBvYLd3i0IZo1ajjc00yRK3v24VRq9nQpoPLuqyH2jzlhCEjXuPScPbi5KEVs9fNcOTtgzbVf7IG2gNiwNs5aCpN4Bv/Zv2A6zp5xGz9cWj2f0aD9v66vX4bexOs5t/YYhwuwAvkkJPSIGvxja0xRThnceHyFHKtj0H+bi/PWAtlI8YJcDX69cM30JAHDdQH+ltm/4scFptW1hlvMaP+WReCAaCrsHrAT+yka7ttw5YlUyvZ8EPog+j6fwHlxmrXM9h1BqdikomyJU00gm1++FJelfP+1zAwcyrxCnbRl3ARFrAt8hIlrT6Vyu8WvWtLxcI8KcLcJQb/LgkW+sCTGlYcY8z3zkigJMbYn07ewTL5Ss7LazTJJa758I7PZan/v3xQHd5DEc5WBneiV3iOznDFgup0VAMkIviVjVCkszaPSVEdK2NU7jtrh6Jfm7bU/3P6ZG+CkyDLIa8MBn9KPXeJd/y+jTk5Ii+fIwO/+mDpGNUribg6TPxhzZ8b/XdZO1kS1gVgqjXyVC+M+BRBh6C4H21w/eMzjCtDIpoxt5rGKL6Nu/IFMipoC4fgx6LIIHwtGYMG7SWQi7OsMAkiwZRg0n68/RqWgLzBt/4pfjSRYuk=", Don't use a service account token for authentication, Employ least privileged access to AWS Resources, Use IAM Roles when multiple users need identical access to the cluster, Employ least privileged access when creating RoleBindings and ClusterRoleBindings, Create the cluster with a dedicated IAM role, Use tools to make changes to the aws-auth ConfigMap, Alternative Approaches to Authentication and Access Management, Update the aws-node daemonset to use IRSA, Restrict access to the instance profile assigned to the worker node, Scope the IAM Role trust policy for IRSA to the service account name, When your application needs access to IMDS, use IMDSv2 and increase the hop limit on EC2 instances to 2, Disable auto-mounting of service account tokens, Use dedicated service accounts for each application, Grant least privileged access to applications, Review and revoke unnecessary anonymous access, https://docs.aws.amazon.com/STS/latest/APIReference/API_GetCallerIdentity.html, Authenticating to EKS Using GitHub Credentials with Teleport, Consistent OIDC authentication across multiple EKS clusters using kube-oidc-proxy, Introducing OIDC identity provider authentication for Amazon EKS, Using Dex & dex-k8s-authenticator to authenticate to Amazon EKS, https://kubernetes.io/docs/reference/access-authn-authz/rbac/#service-account-permissions, https://docs.aws.amazon.com/eks/latest/userguide/iam-roles-for-service-accounts-technical-overview.html, Limiting access to the instance metadata service, https://eksctl.io/usage/iamserviceaccounts/, https://docs.aws.amazon.com/eks/latest/userguide/iam-roles-for-service-accounts-minimum-sdk.html, Configure the EKS cluster endpoint to be private. If the request is well-formed, the webhook calls a pre-signed URL embedded in the token's body. Now lets get into the specifics of setting this part up. First, start by creating two IAM roles named eks-admin-role and eks-developer-role with the following CLI commands: aws iam create-role --role-name eks-admin-role --output text --query 'Role.Arn', aws iam create-role --role-name eks-developer-role --output text --query 'Role.Arn'. # Allow user to get, list of watch the pods. Once unsuspended, aws-builders will be able to comment and publish posts again. The controller also needs to be able to invoke AWS APIs to provision and configure an ALB.  If you decide to use this, the AWS CLI v2.0 includes an option to create a named profile that makes it easy to associate an SSO session with your current CLI session and assume an IAM role.
If you decide to use this, the AWS CLI v2.0 includes an option to create a named profile that makes it easy to associate an SSO session with your current CLI session and assume an IAM role. While this allows them to read the web identity token file, running a container as root is not considered a best practice.