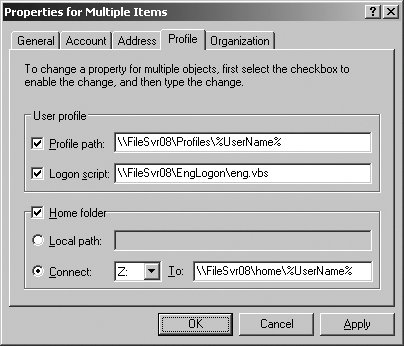
For example - redirect "My Documents" but leave "My Music" local. Prevent users from adding files to the root of their Users Files folder. Connect and share knowledge within a single location that is structured and easy to search. If you disable or do not configure this policy setting, the user's home folder is configured as specified in the user's Active Directory Domain Services account. Restrict unpacking and installation of gadgets that are not digitally signed. content, Turn off Help and Support Center Microsoft Knowledge Base search, Turn off Internet Connection Wizard if URL connection is referring to Microsoft.com, Turn off Internet download for Web publishing and online ordering wizards, Turn off Internet File Association service, Turn off Registration if URL connection is referring to Microsoft.com, Turn off Search Companion content file updates, Turn off the "Publish to Web" task for files and folders, Turn off the Windows Messenger Customer Experience Improvement Program, Turn off Windows Customer Experience Improvement Program, Turn off Windows Network Connectivity Status Indicator active tests, Turn off Windows Update device driver searching, Do not allow changes to initiator iqn name, Do not allow changes to initiator CHAP secret, Do not allow sessions without mutual CHAP, Do not allow sessions without one way CHAP, Do not allow adding new targets via manual configuration, Do not allow manual configuration of discovered targets, Do not allow manual configuration of iSNS servers, Do not allow manual configuration of target portals, KDC support for claims, compound authentication and Kerberos armoring, KDC support for PKInit Freshness Extension, Provide information about previous logons to client computers, Allow retrieving the cloud kerberos ticket during the logon, Always send compound authentication first, Define host name-to-Kerberos realm mappings, Define interoperable Kerberos V5 realm settings, Disable revocation checking for the SSL certificate of KDC proxy servers, Fail authentication requests when Kerberos armoring is not available, Kerberos client support for claims, compound authentication and Kerberos armoring, Require strict target SPN match on remote procedure calls, Set maximum Kerberos SSPI context token buffer size, Specify KDC proxy servers for Kerberos clients, Support device authentication using certificate, Enumeration policy for external devices incompatible with Kernel DMA Protection, Disallow copying of user input methods to the system account for sign-in, Disallow user override of locale settings, Allow users to select when a password is required when resuming from connected standby, Always wait for the network at computer startup and logon, Block user from showing account details on sign-in, Do not display the Getting Started welcome screen at logon, Do not enumerate connected users on domain-joined computers, Enumerate local users on domain-joined computers, Hide entry points for Fast User Switching, Turn off app notifications on the lock screen, Do not process incoming mailslot messages used for domain controller location based on NetBIOS domain names, Do not use NetBIOS-based discovery for domain controller location when DNS-based discovery fails, Set Priority in the DC Locator DNS SRV records, Set Weight in the DC Locator DNS SRV records, Specify address lookup behavior for DC locator ping, Specify DC Locator DNS records not registered by the DCs, Specify dynamic registration of the DC Locator DNS Records, Specify Refresh Interval of the DC Locator DNS records, Specify sites covered by the application directory partition DC Locator DNS SRV records, Specify sites covered by the DC Locator DNS SRV records, Specify sites covered by the GC Locator DNS SRV Records, Use automated site coverage by the DC Locator DNS SRV Records. Historically, network drive space was at a premium so users are in the habit of only putting important files on the network. In the past when creating these manually we would go to the user properties, profile tab, select Connect in the Home folder section, select the drive (H: in this case) and then enter the path of the drive \\server\folder\%username%. However, the setting you described does work. Stack Exchange network consists of 181 Q&A communities including Stack Overflow, the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Whats the purpose of that "Local Path" in the "Home folder"? Asking for help, clarification, or responding to other answers. It only takes a minute to sign up. If the "Set Remote Desktop Services User Home Directory" policy setting is enabled, the "Set user home folder" policy setting has no effect. What am I missing?  If you choose "On the network," enter the path to a file share in the Path box (for example, \\ComputerName\ShareName), and then choose the drive letter to assign to the file share. How can one check whether tax money is being effectively used by the government for improving a nation? Click Permissions, Step 5: Select Everyone under Group or user names and click Remove. Have a great day, I know I will! Site design / logo 2022 Stack Exchange Inc; user contributions licensed under CC BY-SA. Busting at the edges and running towards technology as fast as we can. I just wanted to start today's edition of the Snap! Interestingly this happens even when a folder does get created for the user. I'd appreciate if someone clarify to me the use of "Local Path" and how to use it? Note: The Drive letter box is ignored if you choose "On the local computer" from the Location list. Making statements based on opinion; back them up with references or personal experience. Register domain joined computers as devices, Configure the server address, refresh interval, and issuer certificate authority of a target Subscription Manager, Control Event Log behavior when the log file reaches its maximum size, Events.asp program command line parameters, Hide previous versions list for local files, Hide previous versions list for remote files, Hide previous versions of files on backup location, Prevent restoring local previous versions, Prevent restoring previous versions from backups, Prevent restoring remote previous versions, Allow the use of remote paths in file shortcut icons. Normally the user folder will be created if you create a new user in AD UC. I have always, across the majority of networks I've been in charge of, connected the Home folder in AD to a network share
Disable binding directly to IPropertySetStorage without intermediate layers.
If you choose "On the network," enter the path to a file share in the Path box (for example, \\ComputerName\ShareName), and then choose the drive letter to assign to the file share. How can one check whether tax money is being effectively used by the government for improving a nation? Click Permissions, Step 5: Select Everyone under Group or user names and click Remove. Have a great day, I know I will! Site design / logo 2022 Stack Exchange Inc; user contributions licensed under CC BY-SA. Busting at the edges and running towards technology as fast as we can. I just wanted to start today's edition of the Snap! Interestingly this happens even when a folder does get created for the user. I'd appreciate if someone clarify to me the use of "Local Path" and how to use it? Note: The Drive letter box is ignored if you choose "On the local computer" from the Location list. Making statements based on opinion; back them up with references or personal experience. Register domain joined computers as devices, Configure the server address, refresh interval, and issuer certificate authority of a target Subscription Manager, Control Event Log behavior when the log file reaches its maximum size, Events.asp program command line parameters, Hide previous versions list for local files, Hide previous versions list for remote files, Hide previous versions of files on backup location, Prevent restoring local previous versions, Prevent restoring previous versions from backups, Prevent restoring remote previous versions, Allow the use of remote paths in file shortcut icons. Normally the user folder will be created if you create a new user in AD UC. I have always, across the majority of networks I've been in charge of, connected the Home folder in AD to a network share
Disable binding directly to IPropertySetStorage without intermediate layers.
Use DNS name resolution with a single-label domain name instead of NetBIOS name resolution to locate the DC, Allow cryptography algorithms compatible with Windows NT 4.0, Specify negative DC Discovery cache setting, Specify positive periodic DC Cache refresh for non-background callers, Use final DC discovery retry setting for background callers, Use initial DC discovery retry setting for background callers, Use maximum DC discovery retry interval setting for background callers, Use positive periodic DC cache refresh for background callers, Use urgent mode when pinging domain controllers, Allow Clipboard synchronization across devices, Select the lid switch action (on battery), Select the lid switch action (plugged in), Select the Power button action (on battery), Select the Power button action (plugged in), Select the Sleep button action (on battery), Select the Sleep button action (plugged in), Select the Start menu Power button action (on battery), Select the Start menu Power button action (plugged in), Energy Saver Battery Threshold (on battery), Energy Saver Battery Threshold (plugged in), Allow applications to prevent automatic sleep (on battery), Allow applications to prevent automatic sleep (plugged in), Allow automatic sleep with Open Network Files (on battery), Allow automatic sleep with Open Network Files (plugged in), Allow network connectivity during connected-standby (on battery), Allow network connectivity during connected-standby (plugged in), Allow standby states (S1-S3) when sleeping (on battery), Allow standby states (S1-S3) when sleeping (plugged in), Require a password when a computer wakes (on battery), Require a password when a computer wakes (plugged in), Specify the system hibernate timeout (on battery), Specify the system hibernate timeout (plugged in), Specify the system sleep timeout (on battery), Specify the system sleep timeout (plugged in), Specify the unattended sleep timeout (on battery), Specify the unattended sleep timeout (plugged in), Turn on the ability for applications to prevent sleep transitions (on battery), Turn on the ability for applications to prevent sleep transitions (plugged in), Specify the display dim brightness (on battery), Specify the display dim brightness (plugged in), Turn off adaptive display timeout (on battery), Turn off adaptive display timeout (plugged in), Turn on desktop background slideshow (on battery), Turn on desktop background slideshow (plugged in), Minimum Idle Connection Timeout for RPC/HTTP connections, Propagation of extended error information, Restrictions for Unauthenticated RPC clients, RPC Endpoint Mapper Client Authentication, All Removable Storage: Allow direct access in remote sessions, All Removable Storage classes: Deny all access, Allow logon scripts when NetBIOS or WINS is disabled, Maximum wait time for Group Policy scripts, Run Windows PowerShell scripts first at computer startup, shutdown, Run Windows PowerShell scripts first at user logon, logoff, Configure the refresh interval for Server Manager, Do not display Initial Configuration Tasks window automatically at logon, Do not display Server Manager automatically at logon, Turn off automatic termination of applications that block or cancel shutdown, Allow downloading updates to the Disk Failure Prediction Model, Allow Storage Sense Temporary Files cleanup, Configure Storage Sense Cloud Content dehydration threshold, Configure Storage Sense Recycle Bin cleanup threshold, Configure Storage Storage Downloads cleanup threshold, Detect application failures caused by deprecated COM objects, Detect application failures caused by deprecated Windows DLLs, Detect application installers that need to be run as administrator, Detect applications unable to launch installers under UAC, Detect compatibility issues for applications and drivers, Configure Corrupted File Recovery Behavior, Disk Diagnostic: Configure custom alert text, Disk Diagnostic: Configure execution level, Microsoft Support Diagnostic Tool: Configure execution level, Microsoft Support Diagnostic Tool: Restrict tool download, Microsoft Support Diagnostic Tool: Turn on MSDT interactive communication with support provider, Troubleshooting: Allow users to access recommended troubleshooting for known problems, Configure MSI Corrupted File Recovery Behavior, Configure Security Policy for Scripted Diagnostics, Troubleshooting: Allow users to access and run Troubleshooting Wizards, Troubleshooting: Allow users to access online troubleshooting content on Microsoft servers from the Troubleshooting Control Panel (via the Windows Online Troubleshooting Service - WOTS), Diagnostics: Configure scenario execution level, Diagnostics: Configure scenario retention, Configure the level of TPM owner authorization information available to the operating system, Configure the list of blocked TPM commands. Hide the TPM Firmware Update recommendation. I use GPP to link to home folders and other mapped drives, but I have to create the home folders manually now. Do not prompt for client certificate selection when no certificates or only one certificate exists. I maybe totally wrong but I was expecting the users data to be saved in "C:\UserData" instead of the default My Document folder when saving
Allow Secure Boot for integrity validation, Choose how BitLocker-protected operating system drives can be recovered, Configure pre-boot recovery message and URL, Configure TPM platform validation profile (Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2), Configure TPM platform validation profile for BIOS-based firmware configurations, Configure TPM platform validation profile for native UEFI firmware configurations, Configure use of hardware-based encryption for operating system drives, Configure use of passwords for operating system drives, Disallow standard users from changing the PIN or password, Enable use of BitLocker authentication requiring preboot keyboard input on slates, Enforce drive encryption type on operating system drives, Require additional authentication at startup (Windows Server 2008 and Windows Vista), Require additional authentication at startup, Reset platform validation data after BitLocker recovery, Use enhanced Boot Configuration Data validation profile, Allow access to BitLocker-protected removable data drives from earlier versions of Windows, Choose how BitLocker-protected removable drives can be recovered, Configure use of hardware-based encryption for removable data drives, Configure use of passwords for removable data drives, Configure use of smart cards on removable data drives, Control use of BitLocker on removable drives, Deny write access to removable drives not protected by BitLocker, Enforce drive encryption type on removable data drives, Choose default folder for recovery password, Choose drive encryption method and cipher strength (Windows 8, Windows Server 2012, Windows 8.1, Windows Server 2012 R2, Windows 10 [Version 1507]), Choose drive encryption method and cipher strength (Windows 10 [Version 1511] and later), Choose drive encryption method and cipher strength (Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2), Choose how users can recover BitLocker-protected drives (Windows Server 2008 and Windows Vista), Disable new DMA devices when this computer is locked, Provide the unique identifiers for your organization, Store BitLocker recovery information in Active Directory Domain Services (Windows Server 2008 and Windows Vista), Validate smart card certificate usage rule compliance, Do not display the password reveal button, Enumerate administrator accounts on elevation, Prevent the use of security questions for local accounts, Require trusted path for credential entry, Allow device name to be sent in Windows diagnostic data, Configure Authenticated Proxy usage for the Connected User Experience and Telemetry service, Configure collection of browsing data for Desktop Analytics, Configure Connected User Experiences and Telemetry, Configure diagnostic data upload endpoint for Desktop Analytics. Send all sites not included in the Enterprise Mode Site List to Microsoft Edge. Ignore the default list of blocked TPM commands, Ignore the local list of blocked TPM commands, Standard User Individual Lockout Threshold, Turn on TPM backup to Active Directory Domain Services, Add the Administrators security group to roaming user profiles, Control slow network connection timeout for user profiles, Delete user profiles older than a specified number of days on system restart, Disable detection of slow network connections, Do not check for user ownership of Roaming Profile Folders, Do not forcefully unload the users registry at user logoff, Do not log users on with temporary profiles, Download roaming profiles on primary computers only, Leave Windows Installer and Group Policy Software Installation Data, Maximum retries to unload and update user profile, Prevent Roaming Profile changes from propagating to the server, Prompt user when a slow network connection is detected, Set maximum wait time for the network if a user has a roaming user profile or remote home directory, Set roaming profile path for all users logging onto this computer, Set the schedule for background upload of a roaming user profile's registry file while user is logged on, User management of sharing user name, account picture, and domain information with apps (not desktop apps), Specify Windows File Protection cache location, Activate Shutdown Event Tracker System State Data feature, Allow Distributed Link Tracking clients to use domain resources, Do not automatically encrypt files moved to encrypted folders, Do not display Manage Your Server page at logon. Keep favorites in sync between Internet Explorer and Microsoft Edge, Prevent access to the about:flags page in Microsoft Edge, Prevent bypassing Windows Defender SmartScreen prompts for files, Prevent bypassing Windows Defender SmartScreen prompts for sites, Prevent changes to Favorites on Microsoft Edge, Prevent Microsoft Edge from gathering Live Tile information when pinning a site to Start, Prevent Microsoft Edge from starting and loading the Start and New Tab page at Windows startup and each time Microsoft Edge is closed, Prevent the First Run webpage from opening on Microsoft Edge, Prevent using Localhost IP address for WebRTC, Send all intranet sites to Internet Explorer 11, Show message when opening sites in Internet Explorer, Suppress the display of Edge Deprecation Notification, Allow companion device for secondary authentication, Microsoft Office 365 SharePoint Designer 2013, Ping the settings storage location before sync, Sync settings over metered connections even when roaming, Use User Experience Virtualization (UE-V), Prevent OneDrive files from syncing over metered connections, Prevent OneDrive from generating network traffic until the user signs in to OneDrive, Prevent the usage of OneDrive for file storage, Prevent the usage of OneDrive for file storage on Windows 8.1, Don't launch privacy settings experience on user logon, Make Parental Controls control panel visible on a Domain, Allow hibernate (S4) when starting from a Windows To Go workspace, Disallow standby sleep states (S1-S3) when starting from a Windows to Go workspace, Allow RDP redirection of other supported RemoteFX USB devices from this computer, Allow .rdp files from valid publishers and user's default .rdp settings, Configure server authentication for client, Do not allow hardware accelerated decoding, Prompt for credentials on the client computer, Specify SHA1 thumbprints of certificates representing trusted .rdp publishers, Do not use Remote Desktop Session Host server IP address when virtual IP address is not available, Select the network adapter to be used for Remote Desktop IP Virtualization, Turn off Windows Installer RDS Compatibility, Allow users to connect remotely by using Remote Desktop Services, Deny logoff of an administrator logged in to the console session, Restrict Remote Desktop Services users to a single Remote Desktop Services session, Set rules for remote control of Remote Desktop Services user sessions, Suspend user sign-in to complete app registration, Allow audio and video playback redirection, Do not allow smart card device redirection, Do not allow supported Plug and Play device redirection, Hide notifications about RD Licensing problems that affect the RD Session Host server, Use the specified Remote Desktop license servers, Do not set default client printer to be default printer in a session, Specify RD Session Host server fallback printer driver behavior, Use Remote Desktop Easy Print printer driver first, Limit the size of the entire roaming user profile cache, Set path for Remote Desktop Services Roaming User Profile, Set Remote Desktop Services User Home Directory, Use mandatory profiles on the RD Session Host server, Configure RD Connection Broker server name, Optimize visual experience for Remote Desktop Service Sessions, Optimize visual experience when using RemoteFX, Allow desktop composition for remote desktop sessions, Configure H.264/AVC hardware encoding for Remote Desktop Connections, Configure image quality for RemoteFX Adaptive Graphics, Enable RemoteFX encoding for RemoteFX clients designed for Windows Server 2008 R2 SP1, Enforce Removal of Remote Desktop Wallpaper, Prioritize H.264/AVC 444 graphics mode for Remote Desktop Connections, Remove "Disconnect" option from Shut Down dialog, Remove Windows Security item from Start menu, Use advanced RemoteFX graphics for RemoteApp, Use hardware graphics adapters for all Remote Desktop Services sessions, Use the hardware default graphics adapter for all Remote Desktop Services sessions, Use WDDM graphics display driver for Remote Desktop Connections, Always prompt for password upon connection, Do not allow local administrators to customize permissions, Require use of specific security layer for remote (RDP) connections, Require user authentication for remote connections by using Network Level Authentication, Server authentication certificate template, Set time limit for active but idle Remote Desktop Services sessions, Set time limit for active Remote Desktop Services sessions, Set time limit for logoff of RemoteApp sessions, Prevent automatic discovery of feeds and Web Slices, Prevent subscribing to or deleting a feed or a Web Slice, Turn off background synchronization for feeds and Web Slices, Turn on Basic feed authentication over HTTP, Force TIFF IFilter to perform OCR for every page in a TIFF document, Allow Cortana Page in OOBE on an AAD account, Always use automatic language detection when indexing content and properties, Don't search the web or display web results in Search, Don't search the web or display web results in Search over metered connections, Do not allow locations on removable drives to be added to libraries, Enable indexing of online delegate mailboxes, Enable indexing uncached Exchange folders, Enable throttling for online mail indexing, Prevent adding UNC locations to index from Control Panel, Prevent adding user-specified locations to the All Locations menu, Prevent automatically adding shared folders to the Windows Search index, Prevent clients from querying the index remotely, Prevent customization of indexed locations in Control Panel, Prevent indexing files in offline files cache, Prevent indexing Microsoft Office Outlook, Prevent indexing when running on battery power to conserve energy, Prevent the display of advanced indexing options for Windows Search in the Control Panel, Prevent unwanted iFilters and protocol handlers, Set large or small icon view in desktop search results, Stop indexing in the event of limited hard drive space, Turn on Security Center (Domain PCs only), Timeout for hung logon sessions during shutdown, Turn off legacy remote shutdown interface, Allow certificates with no extended key usage certificate attribute, Allow ECC certificates to be used for logon and authentication, Allow Integrated Unblock screen to be displayed at the time of logon, Display string when smart card is blocked, Force the reading of all certificates from the smart card, Notify user of successful smart card driver installation, Prevent plaintext PINs from being returned by Credential Manager, Reverse the subject name stored in a certificate when displaying, Turn on certificate propagation from smart card, Turn on root certificate propagation from smart card, Control Device Reactivation for Retail devices, Turn off KMS Client Online AVS Validation, Only display the private store within the Microsoft Store, Turn off Automatic Download and Install of updates, Turn off Automatic Download of updates on Win8 machines, Turn off the offer to update to the latest version of Windows, Do not allow printing to Journal Note Writer, For tablet pen input, don't show the Input Panel icon, For touch input, don't show the Input Panel icon, Include rarely used Chinese, Kanji, or Hanja characters, Turn off AutoComplete integration with Input Panel, Turn off password security in Input Panel, Turn off tolerant and Z-shaped scratch-out gestures, Hide Advanced Properties Checkbox in Add Scheduled Task Wizard, Allow uninstallation of language features when a language is uninstalled, Prohibit installing or uninstalling color profiles, Allow Corporate redirection of Customer Experience Improvement uploads, Tag Windows Customer Experience Improvement data with Study Identifier, Configure Corporate Windows Error Reporting, List of applications to always report errors for, List of applications to never report errors for, Automatically send memory dumps for OS-generated error reports, Prevent display of the user interface for critical errors, Send additional data when on battery power, Send data when on connected to a restricted/costed network, Enables or disables Windows Game Recording and Broadcasting, Allow enumeration of emulated smart card for all users, Use certificate for on-premises authentication, Use cloud trust for on-premises authentication, Use Windows Hello for Business certificates as smart card certificates, Allow suggested apps in Windows Ink Workspace, Allow users to browse for source while elevated, Allow users to use media source while elevated, Control maximum size of baseline file cache, Prevent Internet Explorer security prompt for Windows Installer scripts, Prevent users from using Windows Installer to install updates and upgrades, Prohibit non-administrators from applying vendor signed updates, Save copies of transform files in a secure location on workstation, Specify the types of events Windows Installer records in its transaction log, Turn off creation of System Restore checkpoints, Configure the mode of automatically signing in and locking last interactive user after a restart or cold boot, Disable or enable software Secure Attention Sequence, Display information about previous logons during user logon, Report when logon server was not available during user logon, Sign-in and lock last interactive user automatically after a restart, Prevent Windows Media DRM Internet Access, Prevent Quick Launch Toolbar Shortcut Creation, Do not automatically start Windows Messenger initially, Set the default source path for Update-Help, Allow remote server management through WinRM, Disallow WinRM from storing RunAs credentials, Specify channel binding token hardening level, Specify maximum amount of memory in MB per Shell, Specify maximum number of processes per Shell, Specify maximum number of remote shells per user, Hide the Device performance and health area, Hide the Security processor (TPM) troubleshooter page.